There is commonly some excess step or two necessary to adopt a safer method of working. And most people do not like it. They actually desire decreased safety and The shortage of friction. Which is human nature.
SSH, or safe shell, is undoubtedly an encrypted protocol used to administer and talk to servers. When working with a Linux server you might often expend Considerably of your time inside of a terminal session linked to your server via SSH.
Should the concept is effectively decrypted, the server grants the person access with no need of the password. When authenticated, users can start a remote shell session inside their community terminal to deliver textual content-based mostly commands to your remote server.
For this tutorial We'll use macOS's Keychain Accessibility plan. Commence by including your crucial on the Keychain Accessibility by passing -K choice to the ssh-insert command:
They are asked for their password, they enter it, and they are connected to Sulaco. Their command line prompt improvements to verify this.
Thus it is not recommended to train your customers to blindly take them. Changing the keys is So possibly very best accomplished applying an SSH critical administration Device that also improvements them on customers, or applying certificates.
Should you made your crucial with another identify, or In case you are introducing an existing critical which includes a different title, swap id_ed25519
We need to install your general public key on Sulaco , the distant Laptop or computer, to ensure that it knows that the general public critical belongs to you personally.
You may well be thinking what pros an SSH vital presents if you continue to ought to enter a passphrase. A number of the advantages are:
Get paid to jot down complex tutorials and select a tech-concentrated charity to get a matching donation.
Find out how to deliver an SSH crucial pair on the Personal computer, which you'll be able to then use to authenticate your connection into a distant server.
When you needed to build numerous keys for different web pages that's effortless too. Say, by way of example, you needed to use the default keys we just produced for your server you have on Digital Ocean, so you preferred to make One more list of keys for GitHub. You would Adhere to the same method as earlier mentioned, but when it arrived time to save lots of your vital you would just give it a different name for example "id_rsa_github" or a little something similar.
If you're a WSL user, You should utilize an analogous method with your WSL put in. In reality, It truly is in essence the same as Together with the Command Prompt Model. Why would you want to do that? For those who generally reside in Linux for command line duties then it just is smart to keep your keys in WSL.
OpenSSH has its personal proprietary certification format, which may be used for signing host certificates or person certificates. For user authentication, the lack of remarkably secure certification authorities combined with The shortcoming to audit who will obtain a server by inspecting the server createssh helps make us recommend from using OpenSSH certificates for consumer authentication.
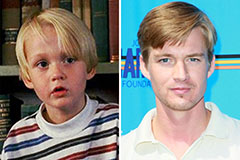 Mason Gamble Then & Now!
Mason Gamble Then & Now! Mackenzie Rosman Then & Now!
Mackenzie Rosman Then & Now! Danielle Fishel Then & Now!
Danielle Fishel Then & Now! Lisa Whelchel Then & Now!
Lisa Whelchel Then & Now! Samantha Fox Then & Now!
Samantha Fox Then & Now!